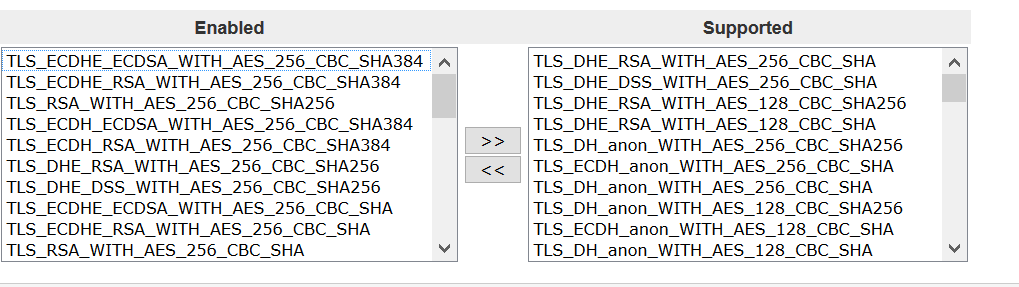
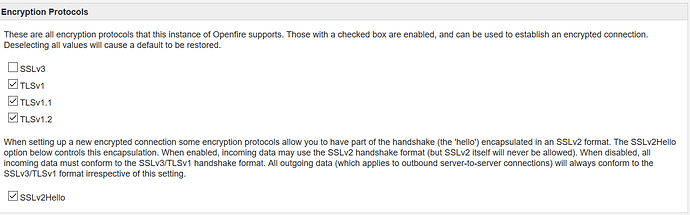
I get this vulnerability when scanning via Nessus.
Vulnerable connection combinations on port 5223/tcp/jabber:
SSL/TLS version : TLSv1.1 Cipher suite : TLS1_CK_DHE_DSS_WITH_AES_128_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources)
SSL/TLS version : TLSv1.1 Cipher suite : TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources)
SSL/TLS version : TLSv1.1 Cipher suite : TLS1_CK_DHE_DSS_WITH_3DES_EDE_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources) SSL/TLS version : TLSv1.0 Cipher suite : TLS1_CK_DHE_DSS_WITH_AES_128_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources) SSL/TLS version : TLSv1.0 Cipher suite : TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources) SSL/TLS version : TLSv1.0 Cipher suite : TLS1_CK_DHE_DSS_WITH_3DES_EDE_CBC_SHA Diffie-Hellman MODP size (bits) : 1024 Warning - This is a known static Oakley Group2 modulus. This may make the remote host more vulnerable to the Logjam attack. Logjam attack difficulty : Hard (would require nation-state resources)
I don’t have these ciphers enabled under client connections, encrypted connection legacy mode for client, advanced. I have TLS1.0, TLS1.1 and TLS1.2 enabled.
Any help would be appreciated.
Thank you.