Hey guys,
i know this is a common thread in this forum and yes, I nearly read everyone of them, but i can´t find a solution.
Hope you can help me, because im stucked in like hell.
First, sry for this long post.
Here are some posts and things i already tried:
Openfire: Overview
SSO problems and a weird REALM
Spark / OpenFire SSO failure
and some more and references from topics etc…
System:
Spark Client on Win7-x64 with jdk/jre1.8.0_66
Openfire on Centos 6.7 with jdk1.8.0
AD on WinServer 2008 R2
The whole Truststructur is on WS2003 and the domain-layer on WS2008 (if necessary to know)
The Spark-Client and the AD-Server are in the same Subnet, the Openfire-Server in another.
Firewall-Rules are already set, so the Openfire-Server can communicate via kerberos to the AD, as well the client can talk to the
Openfire-Server. Only ping does not work (as wanted).
The openfire-server reads the users from AD.
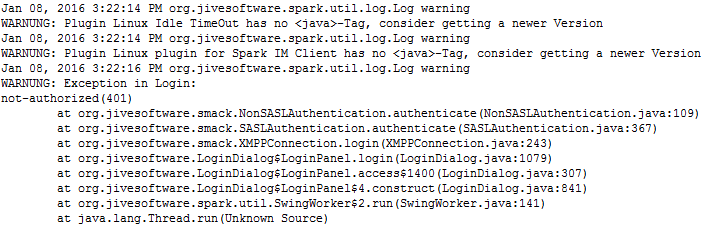
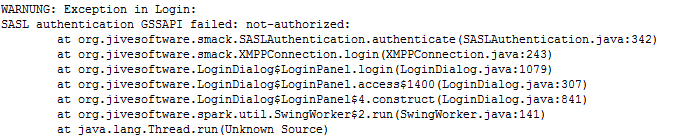
These is the warning from the Spark-Client warn.log:
The errors.log is empty.
This is the output from debug-log "Raw Send Packets:
<stream:stream to=“openfire-server.my.domain” xmlns=“jabber:client” xmlns:stream=“http://etherx.jabber.org/streams” version=“1.0”>
<stream:stream to=“openfire-server.my.domain” xmlns=“jabber:client” xmlns:stream=“http://etherx.jabber.org/streams” version=“1.0”>
AD-User
AD-User
AD-Computer
This is the output from debug-log “Raw Received Packets”:
<?xml version='1.0' encoding='UTF-8'?> <stream:stream xmlns:stream="http://etherx.jabber.org/streams" xmlns="jabber:client" from="**openfire-server.my.domain**" id="7149dd1d" xml:lang="en" version="1.0">
GSSAPI
<compression xmlns="http://jabber.org/features/compress">
zlib
<auth xmlns="http://jabber.org/features/iq-auth"/>
</stream:features>
<?xml version='1.0' encoding='UTF-8'?> <stream:stream xmlns:stream="http://etherx.jabber.org/streams" xmlns="jabber:client" from="**openfire-server.my.domain**" id="7149dd1d" xml:lang="en" version="1.0">
GSSAPI
<compression xmlns="http://jabber.org/features/compress">
zlib
</compression><auth xmlns="http://jabber.org/features/iq-auth"/>
</stream:features>
AD-User
AD-User
AD-Computer
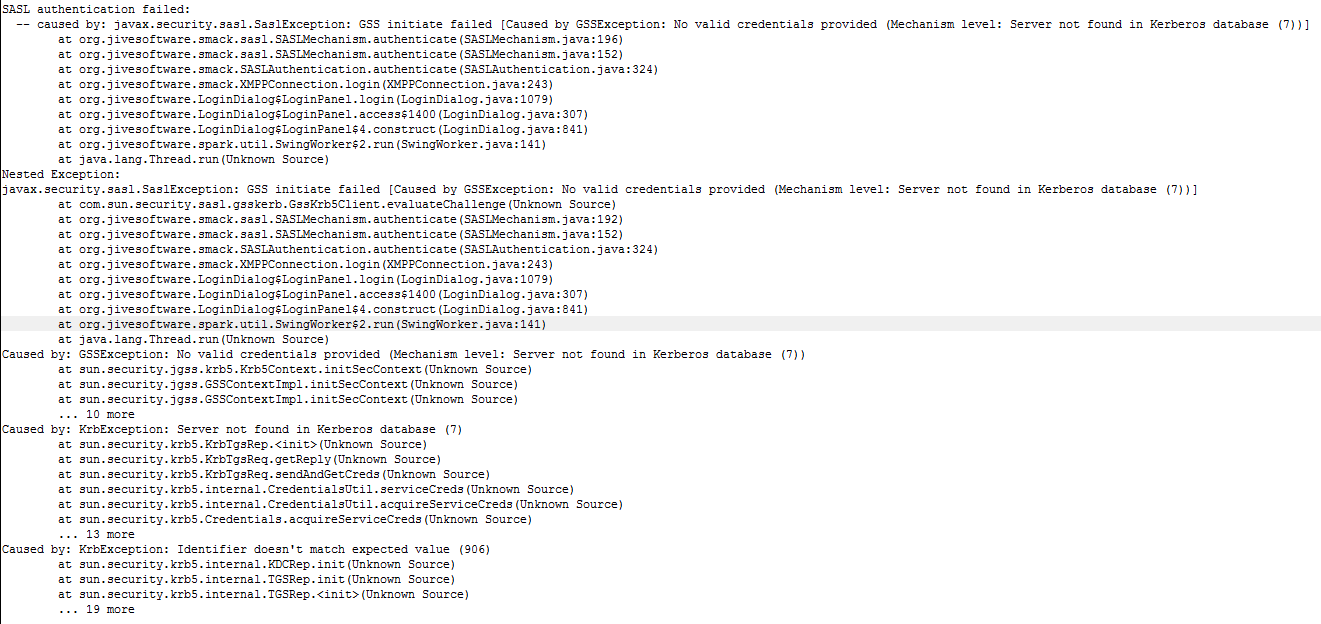
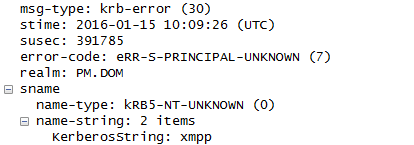
And this is the output from the Openfire-Server debug.log:
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 processing the FINISHED state
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 is now secured
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 processing the FINISHED state
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 is now secured
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Processing the SSL Data
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Message received : HeapBuffer[pos=0 lim=197 cap=512: 17 03 03 00 C0 6B 31 4B 66 A7 6D CC FA 07 6E BB…]
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 Processing the received message
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Processing the SSL Data
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_RECEIVED to session 6
Queue : [MESSAGE_RECEIVED, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_RECEIVED event for session 6
2016.01.08 15:36:41 org.apache.mina.filter.codec.ProtocolCodecFilter - Processing a MESSAGE_RECEIVED for session 6
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Writing Message : WriteRequest: HeapBuffer[pos=0 lim=468 cap=512: 3C 3F 78 6D 6C 20 76 65 72 73 69 6F 6E 3D 27 31…]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_RECEIVED has been fired for session 6
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_SENT to session 6
Queue : [MESSAGE_SENT, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_SENT event for session 6
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_SENT has been fired for session 6
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Message received : HeapBuffer[pos=0 lim=165 cap=256: 17 03 03 00 A0 D9 AE 83 BA 92 27 0E 32 9A 32 70…]
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 Processing the received message
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Processing the SSL Data
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_RECEIVED to session 6
Queue : [MESSAGE_RECEIVED, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_RECEIVED event for session 6
2016.01.08 15:36:41 org.apache.mina.filter.codec.ProtocolCodecFilter - Processing a MESSAGE_RECEIVED for session 6
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Writing Message : WriteRequest: HeapBuffer[pos=0 lim=128 cap=4096: 3C 69 71 20 74 79 70 65 3D 22 72 65 73 75 6C 74…]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_RECEIVED has been fired for session 6
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_SENT to session 6
Queue : [MESSAGE_SENT, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_SENT event for session 6
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_SENT has been fired for session 6
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Message received : HeapBuffer[pos=0 lim=213 cap=256: 17 03 03 00 D0 D2 19 C4 45 C8 CB 2B FB B0 A0 03…]
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslHandler - Session Server6 Processing the received message
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Processing the SSL Data
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_RECEIVED to session 6
Queue : [MESSAGE_RECEIVED, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_RECEIVED event for session 6
2016.01.08 15:36:41 org.apache.mina.filter.codec.ProtocolCodecFilter - Processing a MESSAGE_RECEIVED for session 6
2016.01.08 15:36:41 org.apache.mina.filter.ssl.SslFilter - Session Server6: Writing Message : WriteRequest: HeapBuffer[pos=0 lim=283 cap=4096: 3C 69 71 20 74 79 70 65 3D 22 65 72 72 6F 72 22…]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_RECEIVED has been fired for session 6
2016.01.08 15:36:41 org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_SENT to session 6
Queue : [MESSAGE_SENT, ]
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_SENT event for session 6
2016.01.08 15:36:41 org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_SENT has been fired for session 6
There is no error as you can see. The information, warning and error log from the server are empty, so no problems there as i can imagine.
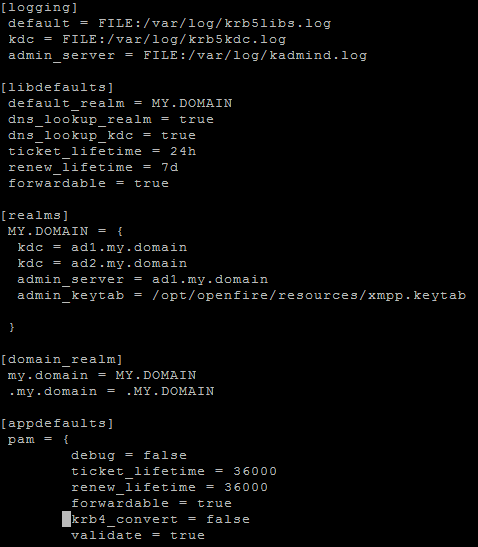
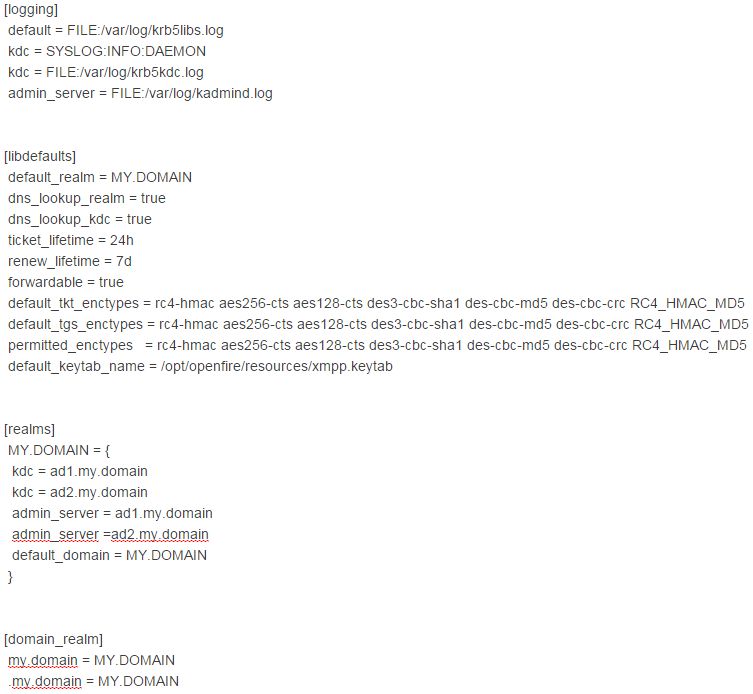
My /etc/krb5.conf:
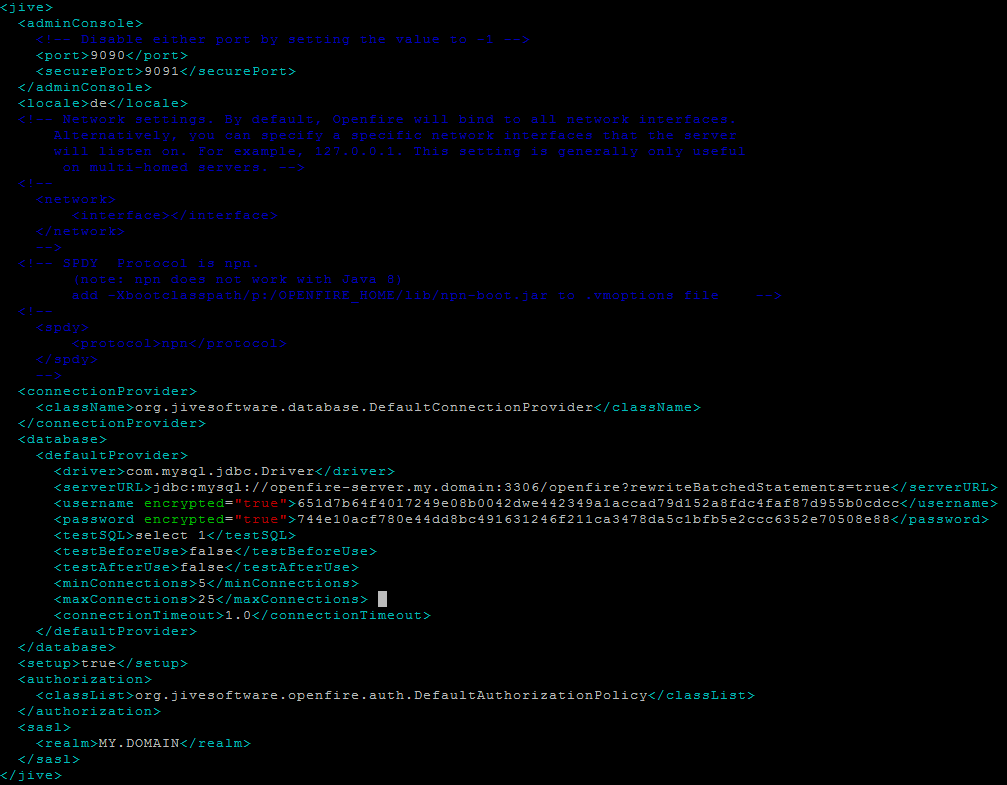
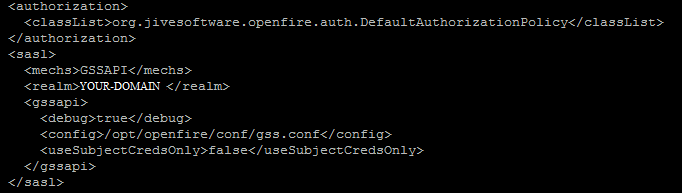
My /opt/openfire/conf/openfire.xml:
The GSSAPI-Configuration are already in the database:
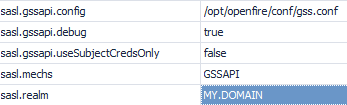
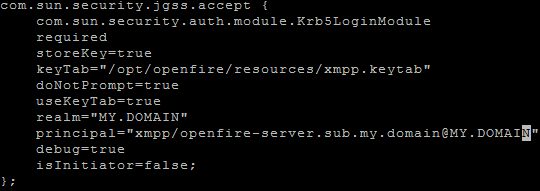
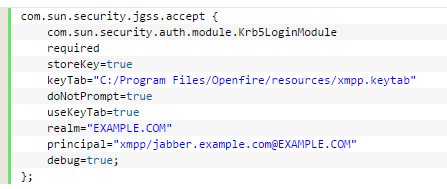
The AD-User for openfire-server “xmpp-openfire” is created and the properties are set as well as the keytab-file is created like it´s mentioned here SSO Configuration .
kinit and klist works on the openfire-server and the spark-client.
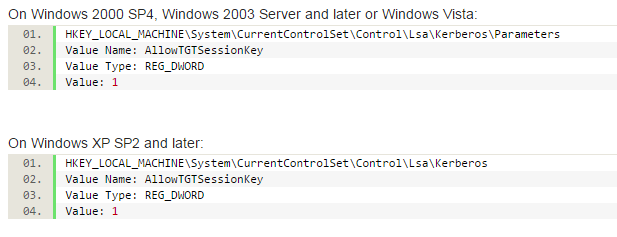
Registry-Entry is done for the client, as well as the sso-Configs (i did them manuell).
Spark-Client get the right account for the User for SSO,… so works well until here.
Did i missed something???
Does anyone have an idea, where the mistake/error is in my configuration so this damn SSO does work?
I should mentioned that normal login via password works well, like always. This was never a problem right
I really could need help